It is not a surprise that anti-forensic techniques are being used by malware writers to increase the examiner’s time. Few weeks ago I was analyzing malware for the customer (the malware has been identified by VirusTotal as Zbot-Trojan). I noticed quite interesting behavior of the malicious code.
The malware self-modify file attributes - MAC times of file which contain malicious code are modified during installation & execution (system startup). This is an example of anti forensic method which makes the creation of Timeline Activity less valuable.
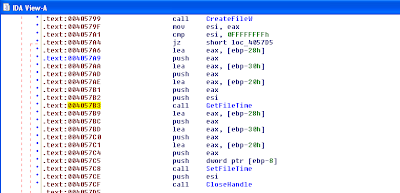
Trojan is using GetFileTIme() and SetFileTime() API which are exported by kernel32.dll. MAC times of malware executable file are set to MAC times of an operating system library – ntdll.dll file.

3 comments:
Setfiletime doesn't affect the MAC times in the filename attributes, does it? I didn't think so, but can't seem to dig up a concrete reference at the moment.
Hi,
SetFileTime function can only set Modified, Accessed and Created times. Common timeline analysis techniques focus on that information. But we have two additional metadata attributes in the MFT - $STANDARD_INFORMATION MFT Modified & $FILE_NAME MFT Modified. This is “time related information from MFT” about which I mentioned above.
Of course it is possible to change all metadata attributes - take a look at the timestomp tool which is part of meterpreter package.
Best regards,
M
This is very useful information. I appreciate your effort for creating this informative blog. Thanks for providing it. Forensic Science College in Madurai
Post a Comment